 All businesses need cybersecurity protection. Most large businesses have a team of IT professionals that know the importance of protecting their business-critical computing infrastructure and resources from everyday cyber-attacks.
All businesses need cybersecurity protection. Most large businesses have a team of IT professionals that know the importance of protecting their business-critical computing infrastructure and resources from everyday cyber-attacks.
But what about you? Why would any hacker want to steal your information? You own a smaller company with fewer employees than the big boys. You have a computer network that’s been running pretty smoothly for several years.
The need for cybersecurity raises a lot of questions. How secure is your IT environment and who is managing it? What do you need to protect? How will you protect data, identities, devices, applications, a reputation, etc? How will you detect a hacking intrusion? What should you do to respond and recover when you are attacked?
Palo Alto Networks made an interesting observation in the 2021 Cortex Xpanse Attack Surface Threat Report. Here is a summary of their key findings: (https://start.paloaltonetworks.com/asm-report)
- Adversaries work to scan the internet for vulnerable systems that are exposed on the internet. A new scan can be done every hour.
- Adversaries are quick to exploit new vulnerabilities. As they become aware of announcements of zero-days and other vulnerabilities, scans begin to find and exploit the vulnerable.
- There is no shortage of vulnerable systems on the World Wide Web.
- Remote access via Remote Desktop Protocol (RDP) is commonly exploited.
- Cloud Computing does not equate to being more secure. ‘Cloud footprints were responsible for 79% of the most critical security issues found.’
Let’s test these key findings:
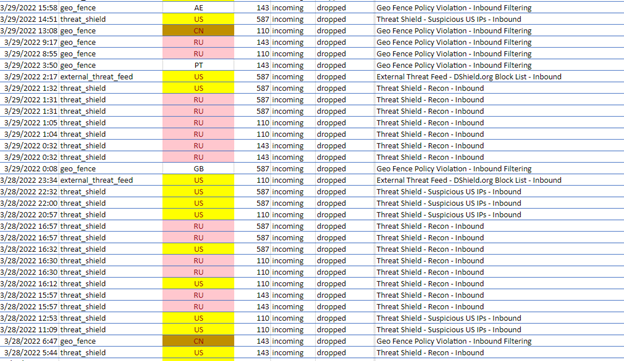
- We pulled and redacted a firewall alert log for the past 30 days and there were over 201K entries. What did we find? Indeed, adversaries are scanning the internet for exposed and vulnerable devices to exploit.
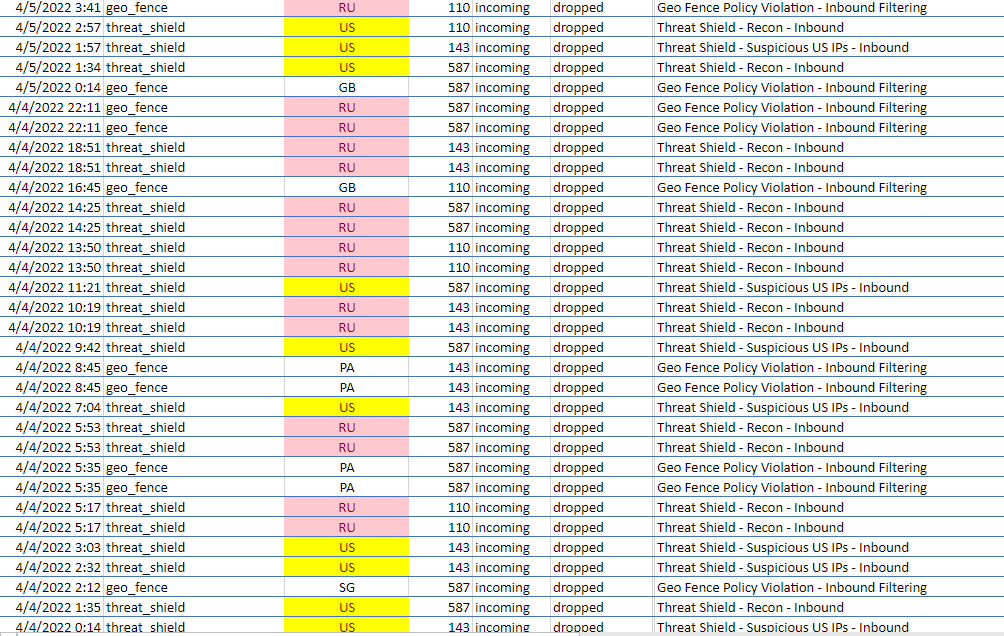
- Remote Desktop Protocol scanning is real and threat actors know that many IT providers will change the port and try to hide the remote access. As you can see, threat actors will scan them all if they have to.
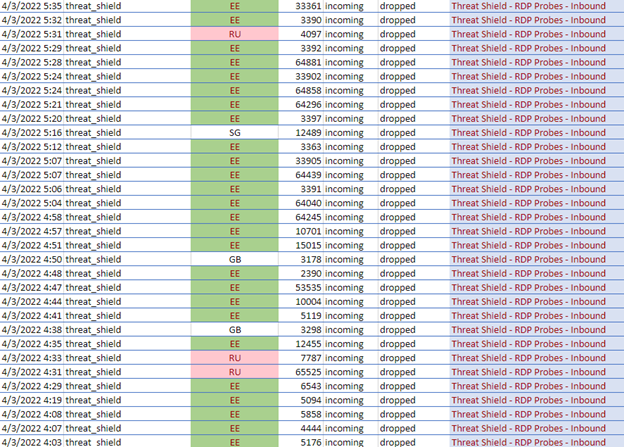
- Email exploitation is high on the list as we see the following mail ports (110, 143, 587) are being scanned. Think of the damage if a mail server is exploited as phishing emails rife with exploits are sent on your behalf, under your nose.
Many business owners are not aware of the risks involved with implementing certain technology and rely on sage consulting advice from their IT professionals. A current search on Shodan, it's like the Google search for IoT (internet of things) devices, and you will find over 21K devices exposed in the Laredo, Texas. These devices vary from security cameras, computers and servers, printers, firewalls, phones, etc. Many have no idea that their login screens, cameras and printers are exposed like this! 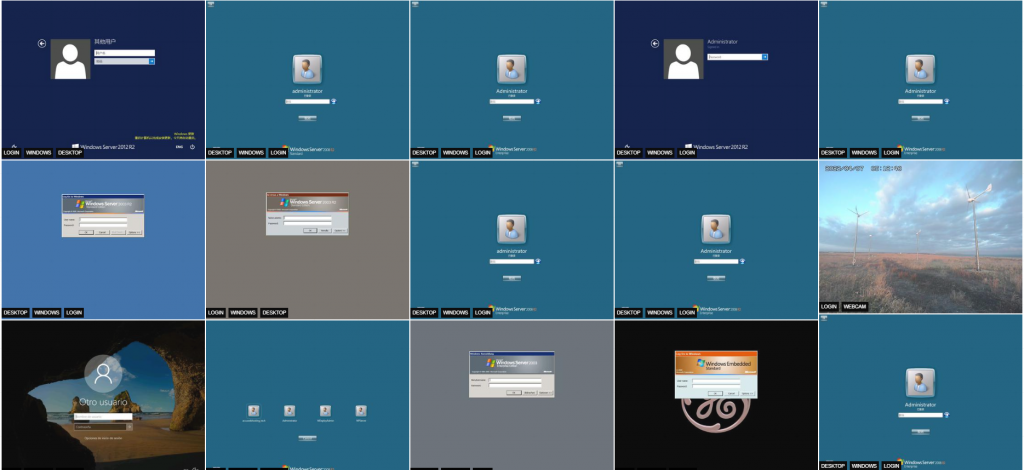
Perhaps there were exposed for convenience. Unfortunately, threat actors are checking all of the doors they come in contact with to see if any of them are open or opened easily and these now become the targeted and anything valuable is exploited and sold and most will never know till it is too late.
The threats are real and we have no idea who will be behind the next incident, hack, compromise or breach nor will we know the reason why and we cannot do anything to stop a threat actor for trying. We can do our part to better secure our businesses and protect our customers by implementing basic security hygiene. Recently, I have heard many talking about a stomach bug and it is spread by unwashed hands after using the restroom...gross! 🤢 🤮 Simply washing hands would do wonders in minimizing sickness but statistics show otherwise. Perhaps hand washing just isn't being done properly. 🙄 🤔
Proper hand washing hygiene and basic security hygiene are possible. They both take a bit more time and add a bit more to the budget and the benefits are much better than not.








