
Have you been seeing an increase in spam and junk email? There was a blog in June 2022, New Phishing Attacks Use HTML Email Attachments. Perhaps, you have seen and email that appears to be from you, but you never sent it and there is an attachment? We have seen an increase being quarantined among our partners. Why the increase and what can you do to better identify them and protect yourself and your business?
Why The increase?
Threat actors are able to take advantage of popular email marketing or relay services and are able to relay messages, spoofing your email. Qakbot seems to be one of the culprits lately. Email is the primarily the way to gain initial access into a business. This is where the attachments come into play and are usually HTML attachments that once accessed will begin to download a compressed file into the user’s download folder. This usually requires user interaction and why being aware of social engineering is so vital. The user is tricked into unzipping or interacting with a shortcut file (.LNK) and the Qakbot begins to make itself at home and becomes a persistent pest, many times evading security products. This Qakbot malware has self-propagating capabilities and can spread quickly through a network. Once downloaded, it will typically invite friends, other malware to install and crash the party. Often it seems as soon as you clean a host, it is re-infected. Qakbot is an information stealer and like we covered in the session can be used to steal information for selling to the highest bidder and does not always result in ransomware.
Identify The Threat
How can you identify such emails? Take a look at the screenshots of redacted emails:
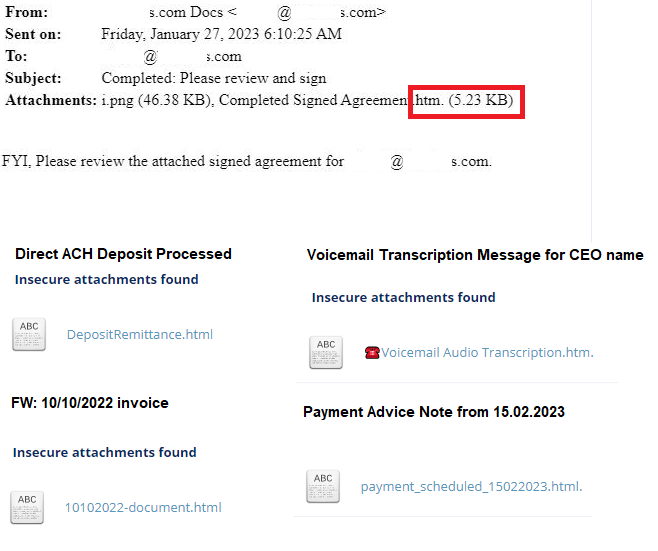
Secure Your Email Defenses
Some time ago, there was an article from our 2021 blog, What Businesses Can Do To Minimize Phishing Emails, that mentioned how DMARC enforcement can virtually eliminate domain spoofing and those emails simply never get delivered. "How effective is that approach? Well, based on the latest statistics, domains without DMARC applied are nearly five times as likely to be the targets of phishing emails compared to those that have it." If order to configure this for your business, you have to have your own email domain. There are certainly many good reasons for owning your own business email domain.
We had a prospect call us one day because someone had gotten access to the gmail account used for the company and began to impersonate this owner. The threat actor was able to change the email to another gmail address within the portal in which the company received freight dispatches. If not stopped, the impersonator could have been on the way to take over as much of the business as possible, locking out the owner.
Would you like to know another reason why you should consider using email from a domain you control? If your employees use free email services for business purposes, such as: gmail, hotmail, outlook, yahoo, etc.; who owns the email address? You or the employee? Whomever controls the email address and that is likely the one using it. How much sensitive information is likely to be contained in those email addresses? How much of it could result in a breach when the employee leaves and has all of the personally identifiable information (PII), patient health information (e-PHI), etc.? Some businesses have their scanners sending such information to these free emails. Can you imagine the damage that could be done?
Invest in a domain and business email that will allow for DMARC, SPF, encryption and security and shrink your business risk profile. If you need assistance, we can help!








